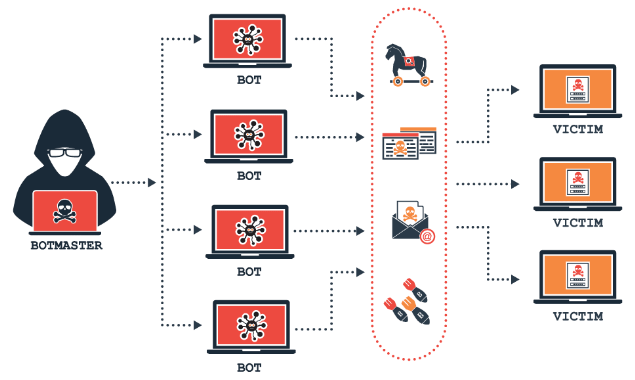
In this article, we will learn about DDoS attacks and their prevention using .NET core.
What is a DDoS (Distributed Denial of Service (DDoS) attack?
When there are millions of requests to a particular server or set of servers, the server becomes too busy to serve the request, in other words, making server overload via sending false or malicious requests. The result of this attack is to make the server unavailable to serve requests or server unavailable.
A DDoS attack aims to disable or take down a website, web application, cloud service, or other online resource by overwhelming it with pointless connection requests, fake packets, or other malicious traffic.
How do you identify if the Server is having such an attack?
A symptom of a DDoS attack is a site or service suddenly becoming slow or unavailable, in this case, further investigation is required to see if there is suspicious traffic or web server has genuine traffic.
- It is required to check logs and traffic analytic tools, which can be used to see the IP address of sources.
- If traffic originates from a single IP address or IP range, then this must be DDoS.
- Odd traffic patterns, such as spikes at odd hours of the day or patterns that appear to be unnatural (e.g., a spike every 10 minutes).
Solution
1. Prevention Technique. Rate Limiter
At the application level, if we want to restrict traffic to an application, we can use Rate Limiter in the .NET core.
In this example, we will configure our service to accept only 20 requests per second, and after that, it will reject or accept any requests.
Steps
Create Web api .net core project.
This is the default template and contains a Weather controller.
Program .cs -> Add the below code.
builder.Services.AddRateLimiter
The method is used to configure and register the rate limiter service with the application’s service container. Once added to the application, the rate limiter can be used to control access to certain routes or endpoints, ensuring that they are not overwhelmed by too many requests.
Now, if we want to set a global rate limiter for all requests, the GlobalLimiter option is set to any PartitionedRateLimiter. In the above example, we have added a FixedWindowLimiter and configured it to apply “per authenticated username (or hostname if not authenticated)” – to the partition. The FixedWindowLimiter is then configured to automatically replenish permitted requests and permits 20 requests per minute.
Testing
I have created a console application that makes http requests to weather API.
- The above code contains a loop for making api calls for 21 times.
- We are logging Console.WriteLine(“Getting response from server ->” + i.ToString());
The above code is making http calls api.
Running the application.
- API
- Console: we can see requests are getting responses till 19 and get exceptions after 19.
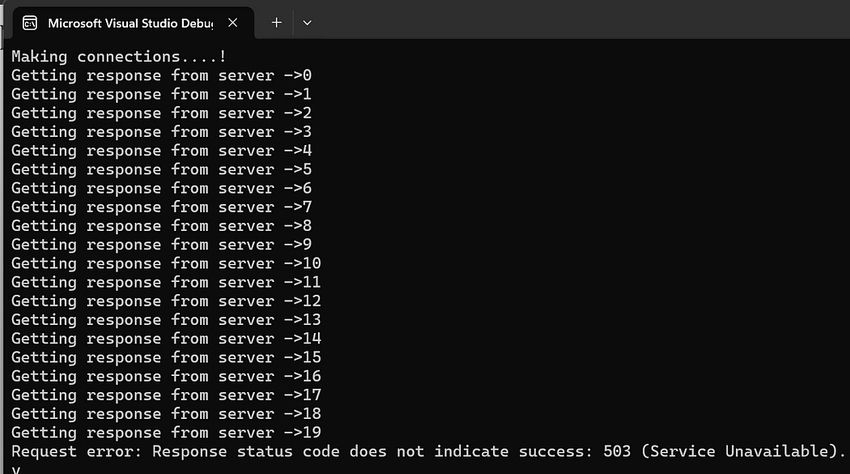
- Specific error code: we can add the code below and get specific exceptions.
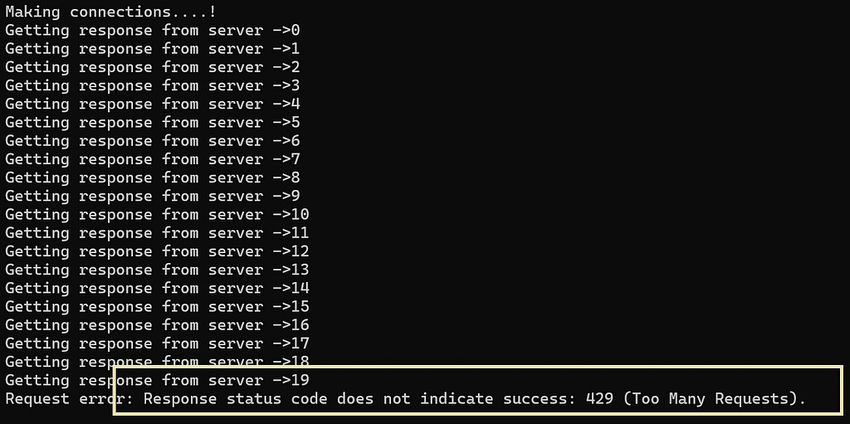
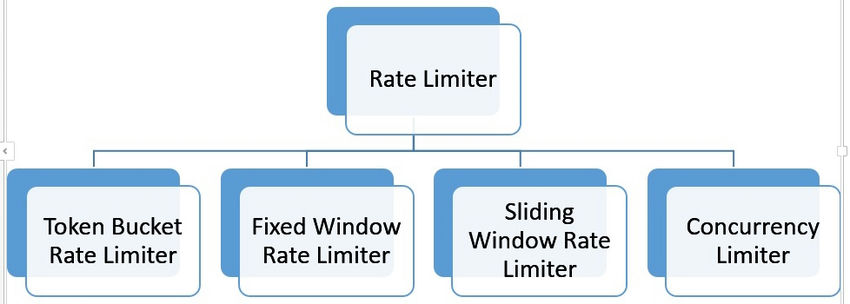
- We have multiple ways to implement rate limiters and have the below types, but I will be explaining them in a separate article.
2. Prevention Technique. IP Blocking and Geo-Blocking
If we know the range of IPs from where we are getting attacks, we can restrict specific IP addresses. We can use the below approach in the .net core.
3. Prevention Technique. Monitoring and Alerting
- We should keep tracing logs using Application Insights to see if we have a lot of requests coming from suspicious IPs.
- Set up alerts for unusual traffic patterns.
4. Prevention Technique. Throttling and Circuit Breaker Patterns
- Implement throttling to control the usage of resources.
- Use libraries like Polly for resilience and transient fault handling.
5. Prevention Technique. Caching
DDoS can also happen in the case of real traffic, in the case of e-commerce sites like Flipkart, Amazon has huge traffic during the sale and if we keep posting a request to servers then servers can be busy resulting in DDoS.
In this case, we can at least apply cache for frequently used data or data from master tables we can limit the number of requests to the server.
6. Prevention Technique. Network Level, Load Balancers, and Firewall’s
DDoS can also happen in the case of real traffic, in the case of e-commerce sites like Flipkart, Amazon has huge traffic during sales and if we keep posting requests to servers then servers can be busy resulting in DDoS.
We can use Azure Load Balancer or AWS Elastic Load Balancing (ELB) to distribute load to multiple servers.
In case of false traffic or malicious traffic, we can implement rules at the network level. Here, we can add rules that can filter the range of IPs and also divert IP addresses to multiple servers.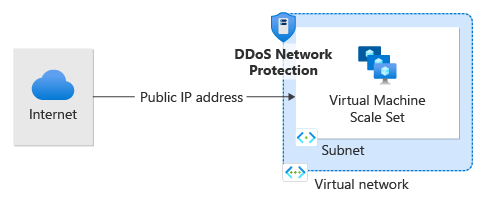
Conclusion
We have covered what DDoS is and the multiple ways to prevent it. Thanks!
Best and Most Recommended ASP.NET Core 8.0.8 Hosting
Fortunately, there are a number of dependable and recommended web hosts available that can help you gain control of your website’s performance and improve your ASP.NET Core 9.0 web ranking. HostForLIFEASP.NET is highly recommended. In Europe, HostForLIFEASP.NET is the most popular option for first-time web hosts searching for an affordable plan.
Their standard price begins at only €3.49 per month. Customers are permitted to choose quarterly and annual plans based on their preferences. HostForLIFEASP.NET guarantees “No Hidden Fees” and an industry-leading ’30 Days Cash Back’ policy. Customers who terminate their service within the first thirty days are eligible for a full refund.
By providing reseller hosting accounts, HostForLIFEASP.NET also gives its consumers the chance to generate income. You can purchase their reseller hosting account, host an unlimited number of websites on it, and even sell some of your hosting space to others. This is one of the most effective methods for making money online. They will take care of all your customers’ hosting needs, so you do not need to fret about hosting-related matters.